Manual
Alarm
Burst Data
Dashboard
Data Source
Manual Inclinometer
Loadsensing
Ackcio
CSI
File Import
Geokon
SAA
Sigicom
Total Stations
Waste Management
Profound
Axilog
GSS
Webcam import
Displacement Graph
GIS
Historical Graphs
Real Time Display
Virtual Variables
SSO
Setup Azure AD for VDV
Setup Single Sign-On in VDV
Single Sign-On setup checklist
Manual provider setup
Analysis
API
Contacts
Contact Groups
Completeness
Data Export Task
Documents
Download Data
Localization
Notes
Month Overview
Reports
Site Setup
QA/QC
Project
Prism
Update Overview
Users in VDV
Manual Import
Setting up a webcam
Embed API
Webcam
User interface
License Overview
Graph Configuration
Site Map
Quick View
Videos
Guides
After install action list
Install VDV on-premise
Creating a new project
Installing scheduled tasks
Restarting the Vista Data Vision System
Exporting site and unit lists from db.robot.c
Exporting the settings from the File Converter
Muting sounds in VDV
Updating VDV with the store in offline mode
Migrate/Move Vista Data Vision to a new server
FAQ
Server Side
File Converter gets empty
Update header - new sensors added to the data file
Import modified or historical data
The VI Not Executable
Email subject contains information from the mail server
Webcam not importing pictures
How to configure Text Message Service
Run tasks minimized
Units
System Requirements
Backing up VDV
Front end
How to extend VDV Timeout
System validation after PHP 8 update
- All Categories
- Manual
- SSO
- Setup Single Sign-On in VDV
Setup Single Sign-On in VDV
The IdP must be configured before the SSO Provider can be created in VDV. Please read Setup Azure AD for VDV or Manual provider setup for instructions.
You'll need the following info before continuing:
- OpenID Connect Metadata URL
- Client ID
- Client Secret
Create new SSO Provider
- Open Setup -> Single Sign On and click the "+" button.
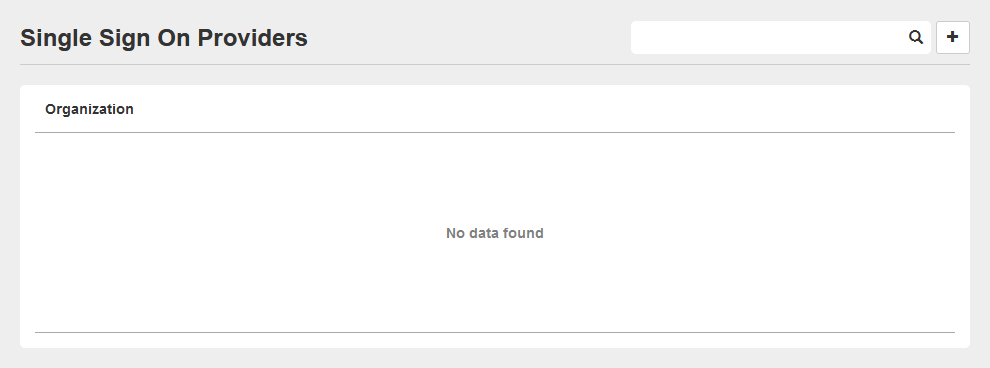
- Select the organization you want to configure SSO for.
Enter the OpenID Connect Metadata URL from before, everything except Client ID and Client Secret will be automatically filled out using the metadata.
Use the Client ID and Secret Value from before.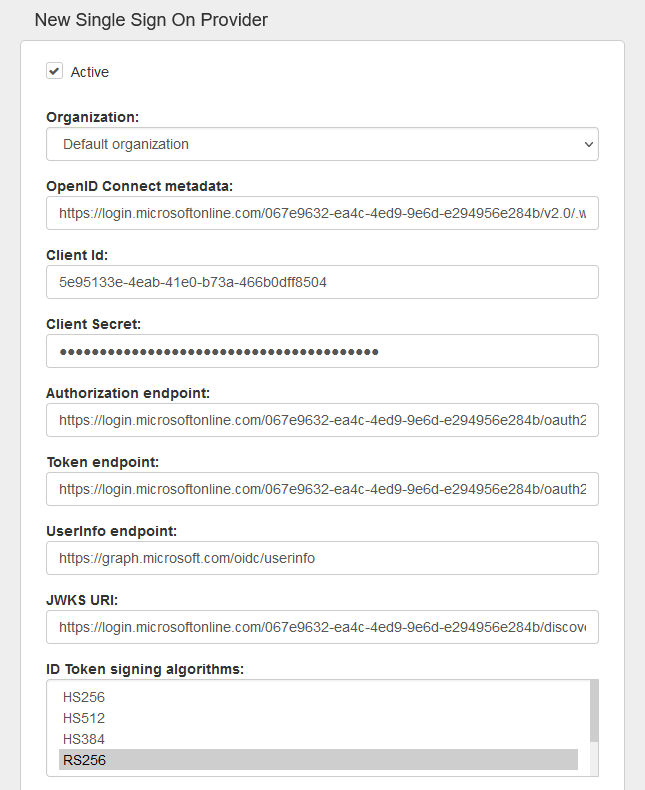
- Select the contact group to send new user notification to and enter a message for new users. This message is shown to users without any projects assigned to them.
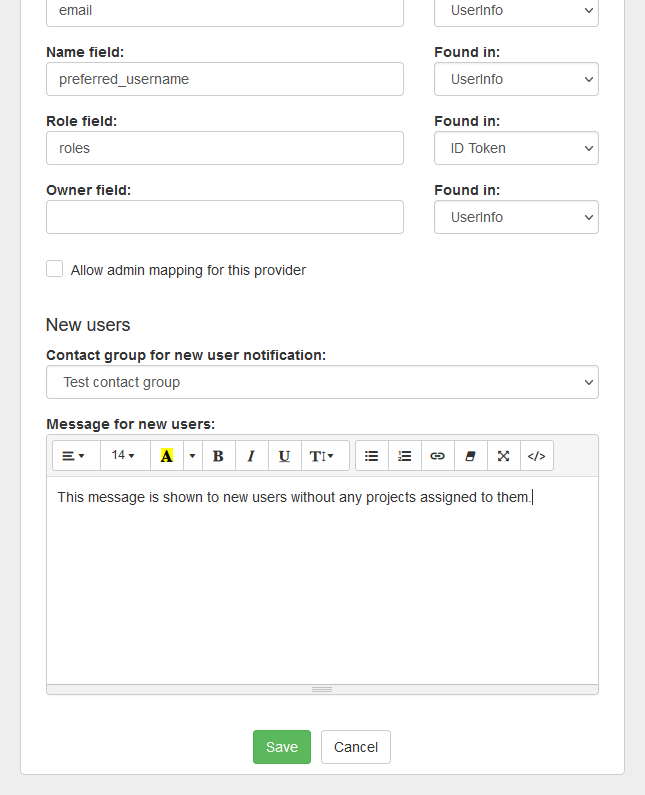
Administration and owning Organization settings

- "Allow admin mapping for this provider". Enabling this options allows specifying an SSO claim to look for and set the user as admin if it's found.
- "Allow admin role for this provider". Enable this to automatically set the user as Admin if they have the given role.
- "Allow all user roles". Enabling this allows the SSO provider to assign all user roles, even those not assigned to the owning Organization.
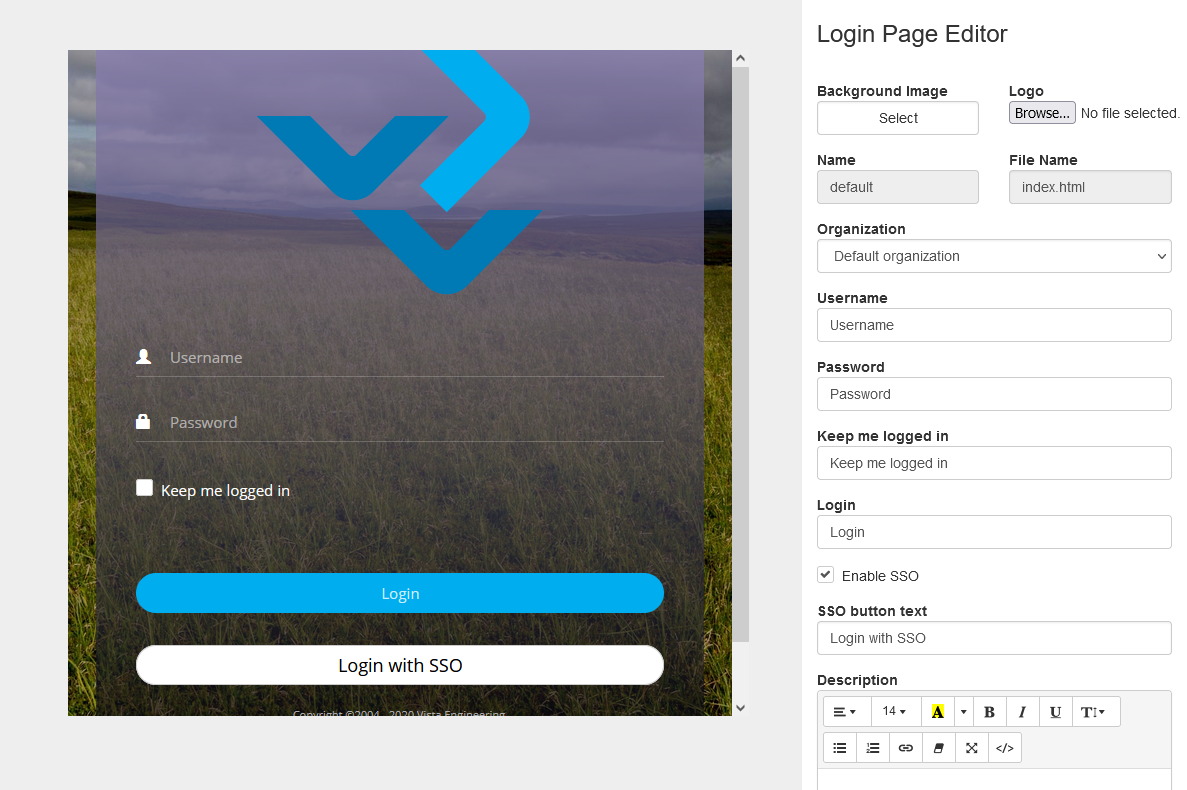
Configure the login page
- Open Setup -> Login Page and click edit on the login page you want to enable SSO or create another one.
- Click the "Enable SSO" checkbox and a new "Login with SSO" button will appear on the login page, the text in the button can be change using the "SSO button text" option.